
Nvidia's $20B Groq Deal: The Inference Wars Just Got Real
Why Nvidia paid 2.9x valuation for a company that claims to be 10x faster than their own GPUs-and what it means for the AI chip market.

Technical explorations and production lessons
I explore modern tech stacks, build things, and document what I learn along the way. From deep dives into new tools to real-world production architectures.


Why Nvidia paid 2.9x valuation for a company that claims to be 10x faster than their own GPUs-and what it means for the AI chip market.

Building Forge, a lightweight local CI/CD tool built with Rust that runs automation pipelines using Docker. Fast, efficient, and no need to push to remote just to test.
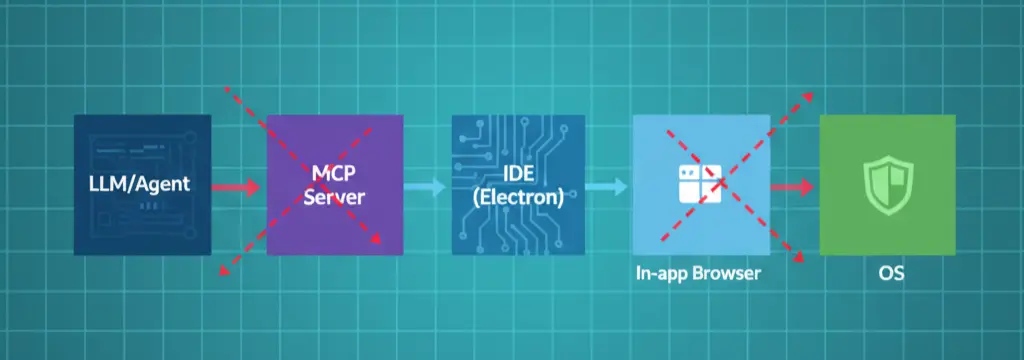
A practitioner’s guide to the Cursor/Windsurf in‑IDE browser takeover class: threat model, safe lab reproduction, generic detections, and an MCP hardening baseline-backed by primary sources.